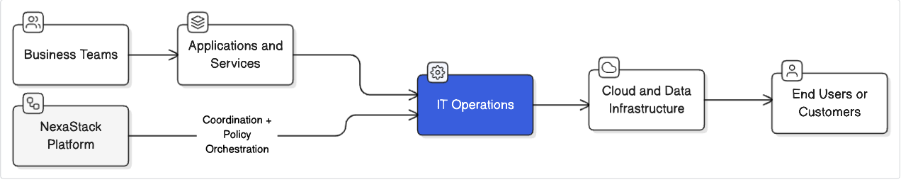
Agentic GRC for Change, Access, and Configuration Governance
Agentic GRC flips the model. Instead of controls waiting to be checked, they are constantly observed, validated, and enforced by agents.
Think of these agents as digital stewards—always watching, always validating, always ensuring alignment with policy and intent. They don’t replace humans—they take over repetitive enforcement work, leaving people to make decisions, rather than chase evidence.
Let’s break down the core areas.
Change Governance
Every organization has change policies—usually documented in ITIL or internal SOPs. However, the real challenge is ensuring that every code deployment, configuration change, infrastructure modification, or permission update adheres to these policies consistently.
Agentic GRC agents:
-
Integrate with CI/CD tools like GitHub Actions, GitLab, Azure DevOps, Jenkins
-
Detect whether a change has the required approval or ticket reference
-
Validate configuration or security compliance before deployment
-
Automatically block, roll back, or quarantine non-compliant changes
-
Log all validation outcomes for audit evidence instantly
Access Governance
Access management has always been a persistent problem. Roles change. Teams shift. Permissions accumulate over time. Over-privileged access is one of the biggest root causes of breaches, according to Microsoft Security.
Agentic GRC automates access governance by:
-
Continuously comparing user access to least-privilege policies
-
Detecting privilege creep and recommending or enforcing rights reduction
-
Automatically removing unused or orphaned accounts
-
Validating privileged access session justification in real time
Instead of quarterly access review meetings, access governance becomes continuous and effortless.
Configuration Governance
Misconfiguration is the silent failure mode of IT environments. AWS and IBM have both published research showing that configuration mistakes—not malware—are the cause of most cloud security incidents.
Agentic GRC agents monitor configurations across:
-
Cloud platforms (AWS, Azure, GCP)
-
Kubernetes clusters and container workloads
-
Firewalls and network controls
-
Identity configurations (Okta, AD, IAM)
-
SaaS and internal business platforms
Whenever a deviation from the approved baseline is detected, the agent can:
-
Auto-remediate instantly
-
Trigger a change request workflow
-
Or escalate to security/IT if human approval is needed
Instead of “configuration is correct during audit season,” it becomes “configuration is correct all the time.”
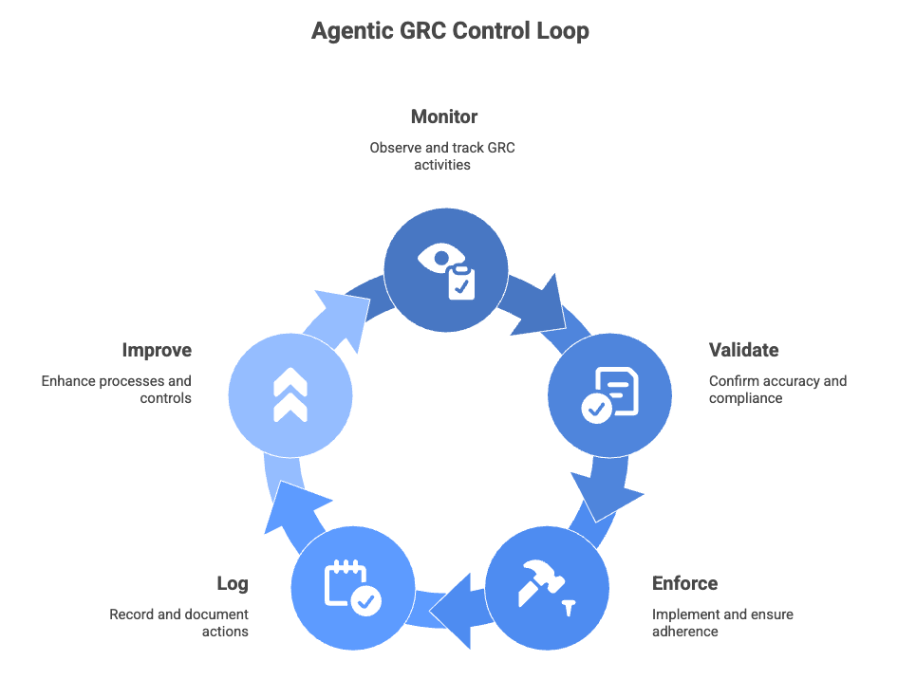
Integration with ITSM and CloudOps Tools for Continuous Compliance
A critical strength of Agentic GRC is that it does not replace existing systems; instead, it complements them. It integrates seamlessly into existing IT workflows.
Integration with ITSM (ServiceNow, Jira Service Management, Freshservice)
Agentic GRC becomes the “intelligent observer” sitting alongside ITSM workflows:
-
When an agent detects a compliance violation, it automatically creates or updates tickets.
-
Ticket status and system state stay synchronized—no guesswork, no chasing.
-
Evidence collection happens as part of the workflow, not after.
This creates traceability without overhead.
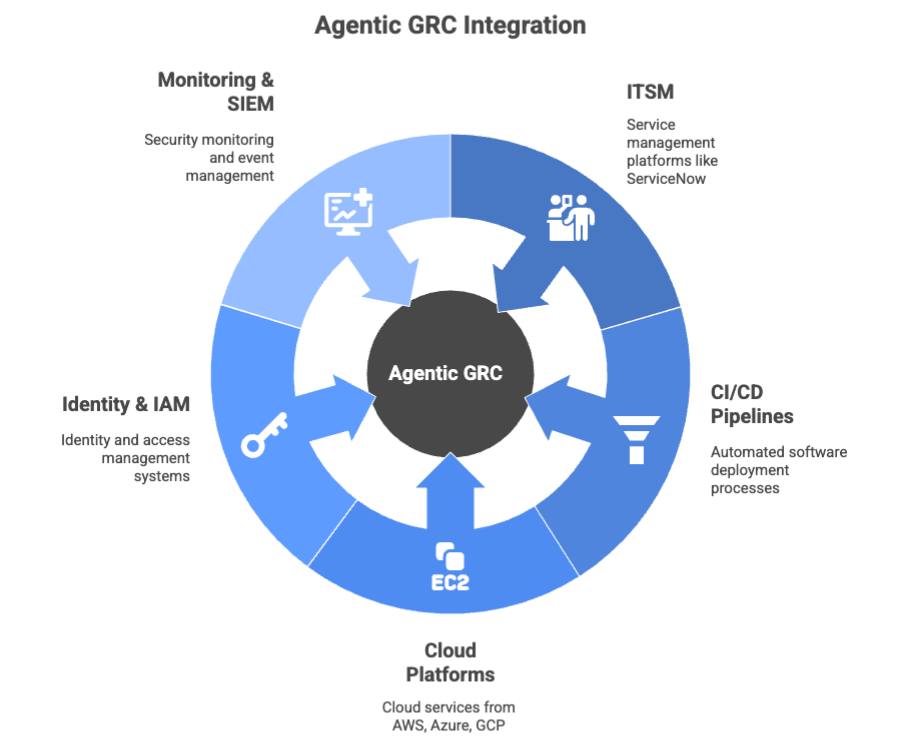
Integration with CloudOps and DevOps Tooling
Agents plug into:
-
Terraform, Pulumi, CloudFormation (to validate IaC before deployment)
-
Kubernetes Admission Controllers (to block non-compliant runtime changes)
-
Monitoring platforms like Datadog, Splunk, and Prometheus (to track operational signals)
-
SIEM/SOAR systems for real-time alerts and automated response
This creates what AWS refers to as guardrails at scale—the cloud runs fast, but never runs outside policy.
Integration with Identity Platforms
By integrating with Azure AD, Okta, Ping, or Keycloak, agents ensure that access remains continuously aligned with business needs—not just role definitions.
This shifts identity governance from a periodic to a dynamic and risk-aware approach.
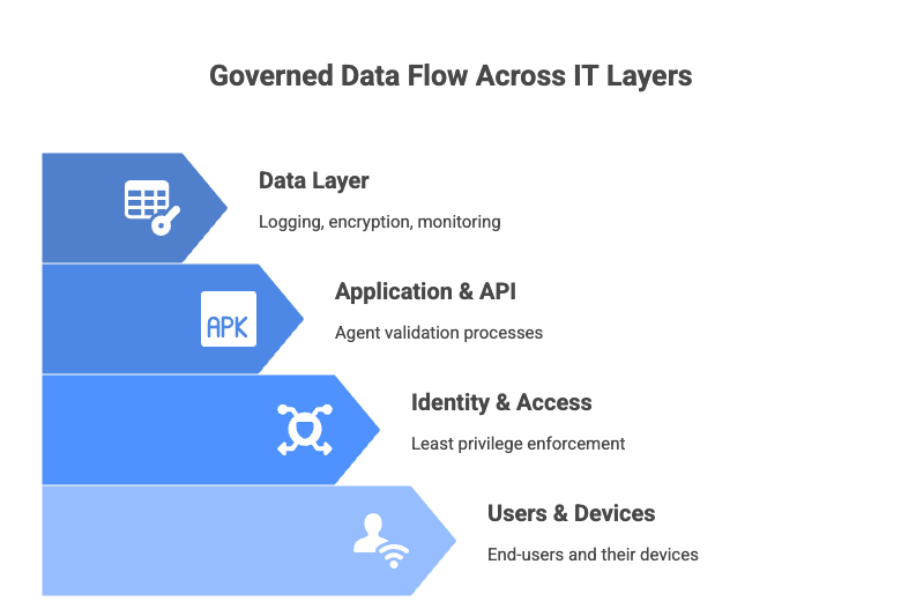
Protecting Data and Information Flow Across IT Layers
Data seldom stays in one system. It moves across services, clouds, apps, APIs, and people.
Agentic GRC monitors and governs data at multiple layers:
Infrastructure Layer
-
Encryption enforcement
-
Secure network zoning
-
Logging and retention integrity
Application Layer
-
Policy-aware API access validation
-
Service-to-service trust enforcement
-
Behavioral monitoring to detect abnormal data flows
User Layer
-
Continuous identity representation checks
-
Context-based access: device, location, behavior pattern
Agentic GRC makes Zero Trust operational in real-time, not just conceptually.
Case Examples – Automating Control Validation and Incident Response
Case 1: Continuous Change Assurance in Cloud Deployments
A financial services company was experiencing configuration drift between environments. Manual checks took hours and were prone to errors.
With Agentic GRC implemented:
-
Every code deployment was automatically scanned against configuration and security baselines.
-
Unauthorized changes were blocked during pipeline execution.
-
DevOps teams no longer had to remember every compliance rule—the system enforced them.
The result: Fewer outages. No last-minute compliance fire drills. Fewer audit findings.
Case 2: Dynamic Access Governance for Internal Teams
An engineering team had accumulated elevated permissions over time due to urgent projects.
Agents detected:
-
Unused admin credentials
-
Stale service accounts
-
Privileged access without linked approval records
The system automatically revoked unneeded access and required justification for any new elevation.
The result: Least privilege restored without political battles or manual reviews.
Case 3: Automated Incident Containment in Real Time
A misconfigured firewall rule unexpectedly exposed an internal API.
Instead of waiting for a human response:
-
An agent detected the anomaly instantly
-
Automatically reverted the change
-
Logged the incident
-
Notified the security team with full context
The exposure window was seconds—not days.
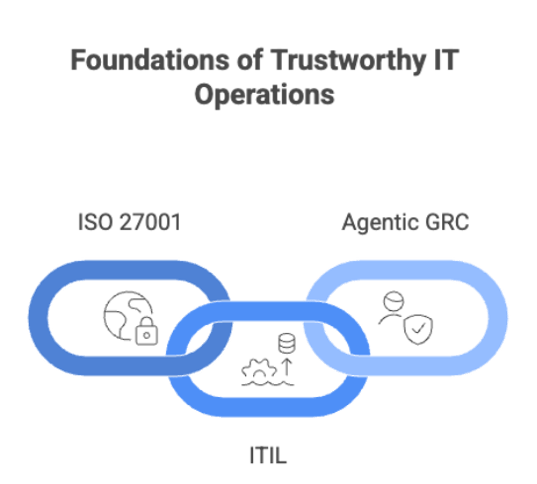
Aligning with ISO 27001 and ITIL for Operational Trust
ISO 27001 and ITIL are two of the most widely recognized frameworks for maintaining secure and reliable IT environments. However, while most organizations document policies based on these standards, the real challenge is ensuring they are followed consistently every day—especially in rapidly evolving cloud and DevOps environments.
This is where Agentic GRC makes a meaningful difference.
Supporting ISO 27001 in Practice
ISO 27001 expects organizations to:
-
Continuously assess risks
-
Maintain secure configurations
-
Control and review access
-
Show evidence that controls are working
Traditionally, these activities require manual reviews, checklists, and audits. Agentic GRC automates them. Agents continuously monitor system state, detect configuration drift, validate access against least-privilege rules, and automatically record evidence as they work.
Strengthening ITIL Service Management
ITIL focuses on operational stability: controlled changes, accurate configurations, and effective incident response. Agentic GRC supports these goals by:
-
Validating changes before deployment
-
Automatically correcting risky or unintended configuration changes
-
Detecting incidents early and triggering guided or automated response steps
This reduces reliance on manual checks or “tribal knowledge,” while still honoring ITIL discipline.
Trustworthy Systems, Not Just Compliant Systems
Compliance alone doesn’t guarantee security—or reliability. However, when controls are enforced continuously and automatically, governance becomes an integral part of operations, rather than a separate burden.
That’s the real outcome of Agentic GRC:
-
Systems stay secure by default
-
Audits become easier
-
Teams work faster with less friction
-
And trust is built into the way IT operates
Agentic GRC doesn’t just help organizations meet standards; it also enables them to exceed expectations.
How NexaStack Powers Agentic GRC in Real Environments
Modern enterprises don’t need another dashboard or monitoring tool—they need a coordination layer that connects systems, enforces controls, and ensures compliance happens continuously, not only during audits.
This is where NexaStack plays a crucial role.
NexaStack provides the underlying execution platform that allows Agentic GRC systems to run autonomously. It acts as the operational backbone that enables agents to:
-
Observe system state across cloud, infrastructure, IAM, ITSM, and Kubernetes environments
-
Reason about compliance drift, misconfigurations, access anomalies, or security risks
-
Act—not just flag violations, but remediate them safely and verifiably
Think of NexaStack as the runtime environment for governance automation, where policies are not just written—they are executed. 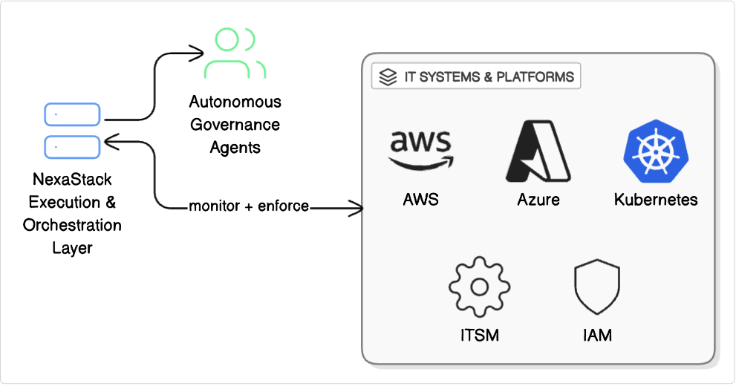
What NexaStack Enables
|
Capability |
How NexaStack Helps |
|
Continuous Compliance |
Agents run constantly in the background, validating controls in real time instead of only during audits. |
|
Zero-Drift Configuration |
Desired-state configurations are automatically enforced across cloud and Kubernetes, reducing the need for manual intervention. |
|
Access Governance |
Any privilege elevation request can trigger automated policy checks and time-bound approvals. |
|
Controlled Change Enforcement |
Changes to infrastructure or applications must align with approved baselines before deployment. |
Instead of waiting for humans to detect issues, NexaStack enables preventive governance:
-
If an S3 bucket becomes public, an agent automatically restricts it.
-
If someone grants themselves admin access → an agent revokes and logs it.
-
If a production configuration drifts, an agent restores the last approved version.
No escalations, no war rooms, no “who changed what” hunting.
Why It Matters
With NexaStack, organizations move from paper compliance to operational trust:
-
Controls are always on
-
Policies are machine-verifiable
-
Compliance artifacts are auto-generated
-
Human teams focus on strategy, not policing
This is what makes Agentic GRC practical, scalable, and enterprise-ready.
Conclusion – Achieving Autonomous IT Assurance
Agentic GRC represents a fundamental shift in how organizations operate:
-
From periodic compliance → to continuous compliance
-
From human monitoring → to autonomous governance agents
-
From reactive incident response → to proactive prevention
-
From manual documentation → to real-time evidence
This doesn’t remove humans—it elevates them.